
COMBATING COMPROMISE
WITH PHISH HUNTER
Phishing campaigns have evolved and become more sophisticated.
What was once easy to single out from legitimate mail due to incorrect grammar or suspicious links and spammed to large numbers of users, has become highly targeted e-mail with skillfully crafted payloads. Sometimes coming from compromised trusted user accounts within an organization.
Confusing the situation more, legitimate e-mail may arrive via third party senders because of corporate use of external SaaS applications, external marketing, electronic signature collection, or other systems.
The question of falling for a phishing email is no longer an “if” but a “when.”
Even the best Secure Email Gateway is not able to catch 100% of attempts, and some attacks will come from inside the organization via legitimate user accounts.
This is where Phish Hunter comes in.
Phish Hunter is a combination of Microsoft cloud security products, custom code, and behavioral analytics that seeks out accounts that may have been compromised and restricts those accounts until they can be reviewed and remediated. Once deployed, Phish Hunter can be tuned to align with the unique way an organization operates to help reduce false positives, and quickly stop further compromise inside an organization.
Phish Hunter takes advantage of security components available in Azure and Office 365 and combines them with Azure Automation and policies customized for your organization.
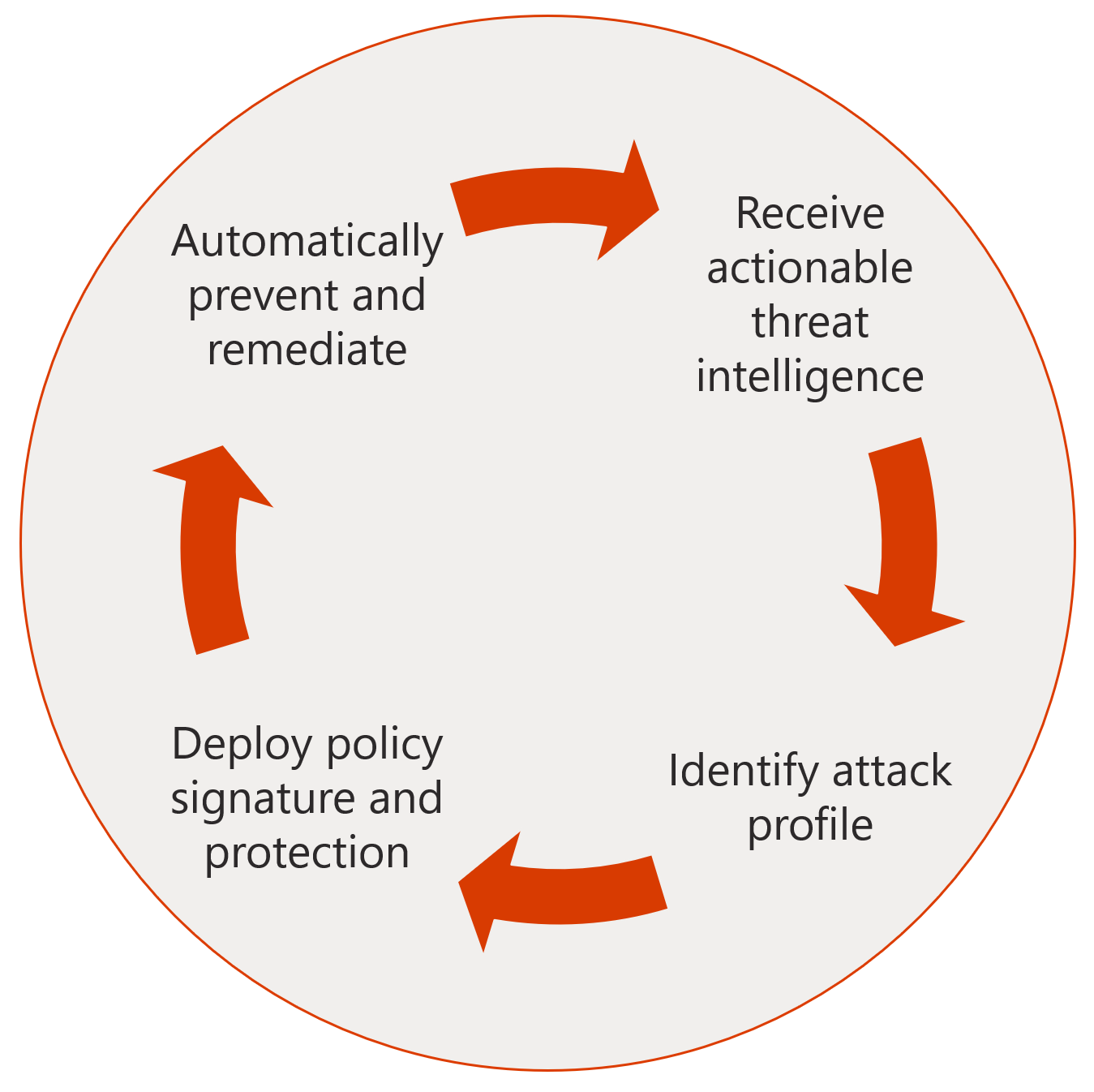
Phish Hunter to the Rescue
B2B was recently certified to deliver Phish Hunter to Microsoft EDU customers. Phish Hunter is a program created by Microsoft to help the K20 community ensure that their Office 365 environment is as secure as possible. It uses Azure Automation to proactively take action when your system is under attack.
Contact B2B Security Experts to help you review your security vulnerabilities and implement a security solution that will reduce current and future vulnerabilities.
For up to date information on phishing attacks and what to do if you have handed over personal or financial information, check wth the FTC (Federal Trade Commission). They also post regularly on phishing attacks found in the wild:
https://www.consumer.ftc.gov/taxonomy/term/1102
Lastly, report phishing emails and texts by forwarding them to spam@uce.gov and filing a report with the FTC.